FBI Investigation Exposes Massive Office365 Executive Email Compromise

Table of Contents
The Scope and Scale of the Office365 Executive Email Compromise
The FBI investigation revealed a widespread campaign targeting high-level executives across various sectors, underscoring the severity of this Office365 executive email compromise. The sheer scale of the breach is alarming, demanding immediate attention from businesses of all sizes.
Number of Affected Organizations
While the exact number of affected organizations remains undisclosed for investigative reasons, sources indicate hundreds of companies across diverse sectors – including finance, healthcare, and technology – have been impacted by this Office365 executive email compromise. The broad reach of the attack emphasizes the indiscriminate nature of these cybercriminal operations, targeting high-value individuals regardless of industry.
Methods Used by Attackers
The attackers employed a multi-pronged approach to compromise Office365 accounts. Their tactics highlight the need for a layered security strategy:
- Phishing campaigns targeting executives: Highly personalized phishing emails, often mimicking legitimate communications from known contacts or organizations, were used to lure executives into revealing their credentials. These emails frequently contained malicious links or attachments.
- Exploiting vulnerabilities in third-party apps integrated with Office365: Attackers exploited vulnerabilities in less secure third-party applications connected to Office365 accounts, gaining unauthorized access through these backdoors. This emphasizes the need for careful vetting of all third-party integrations.
- Credential stuffing and brute-force attacks: Attackers used lists of stolen credentials (credential stuffing) and automated tools (brute-force attacks) to attempt to gain access to accounts with weak or easily guessed passwords.
- Use of malware and advanced persistent threats (APTs): In some cases, the attackers deployed malware to gain persistent access to compromised systems, allowing them to monitor email traffic and exfiltrate sensitive data over extended periods. This points to the increasingly sophisticated nature of these attacks.
Financial Losses and Reputational Damage
The financial losses resulting from this Office365 executive email compromise are substantial, with organizations facing costs associated with incident response, legal fees, and potential regulatory fines. Beyond financial implications, reputational damage can be devastating, eroding customer trust and impacting future business opportunities. The legal ramifications of a data breach, including potential lawsuits and regulatory penalties, further amplify the consequences.
How the Attackers Gained Access: Understanding the Vulnerabilities
The success of this Office365 executive email compromise highlights several critical vulnerabilities that need to be addressed:
Weak Passwords and Phishing
Weak passwords and successful phishing attempts are consistently at the heart of many cyberattacks, and this instance is no different. Many compromised accounts used easily guessed passwords or reused passwords across multiple platforms. Successful phishing campaigns exploited human error, demonstrating the importance of robust security awareness training.
Lack of Multi-Factor Authentication (MFA)
The absence of multi-factor authentication (MFA) significantly increased the vulnerability of Office365 accounts. MFA adds an extra layer of security, requiring users to provide multiple forms of verification to access their accounts, even if their passwords are compromised.
Unpatched Software and Outdated Security Protocols
Using outdated software and neglecting regular security updates creates significant vulnerabilities. Cybercriminals often exploit known security flaws in unpatched software to gain access to systems. Regular patching is crucial to maintaining a strong security posture.
Insider Threats
While not the primary vector in this specific case, the possibility of insider threats contributing to the breach cannot be discounted. Compromised or malicious insiders can provide attackers with valuable access to sensitive information and systems.
Protecting Your Organization from Office365 Executive Email Compromise
Protecting your organization requires a multi-layered approach that addresses the vulnerabilities highlighted in the FBI investigation:
Implementing Strong Password Policies
Enforce strong password policies requiring complex passwords, regular password changes, and password managers. Prohibiting password reuse across multiple platforms is also crucial.
Enforcing Multi-Factor Authentication (MFA)
Mandate the use of multi-factor authentication (MFA) for all Office365 accounts. This adds a significant layer of protection against unauthorized access.
Regular Security Awareness Training
Regular employee training is essential to prevent phishing attacks and educate staff on recognizing and reporting suspicious emails. Simulations and phishing tests can be particularly effective.
Regular Software Updates and Patching
Implement a robust patching schedule to ensure all software, including Office365 and third-party applications, is regularly updated with the latest security patches.
Utilizing Advanced Threat Protection (ATP)
Leverage Office 365's Advanced Threat Protection (ATP) features to detect and prevent malicious emails and attachments before they reach users' inboxes.
Employing Security Information and Event Management (SIEM) tools
Employ SIEM tools to monitor and analyze security logs from various sources, providing early detection of suspicious activity and enabling faster incident response.
Conclusion
The FBI investigation into the massive Office365 executive email compromise underscores the critical need for organizations to strengthen their cybersecurity defenses. The attackers' methods highlighted vulnerabilities in password security, MFA implementation, software updates, and employee awareness. The financial and reputational consequences of such breaches are severe. To avoid becoming a victim, organizations must prioritize implementing robust security measures, including strong passwords, MFA, regular security training, and the utilization of advanced threat protection tools. Don't become the next victim of an Office365 executive email compromise. Take action now to protect your organization from advanced threats. Implement robust security measures today.

Featured Posts
-
 Harnessing Ai To Create Podcasts From Repetitive Scatological Documents
Apr 24, 2025
Harnessing Ai To Create Podcasts From Repetitive Scatological Documents
Apr 24, 2025 -
 High Stock Market Valuations Bof As Analysis And Why Investors Shouldnt Panic
Apr 24, 2025
High Stock Market Valuations Bof As Analysis And Why Investors Shouldnt Panic
Apr 24, 2025 -
 Early Detection Is Key Lessons From Tina Knowles Breast Cancer Journey
Apr 24, 2025
Early Detection Is Key Lessons From Tina Knowles Breast Cancer Journey
Apr 24, 2025 -
 Blue Origin Scraps Rocket Launch Due To Vehicle Subsystem Problem
Apr 24, 2025
Blue Origin Scraps Rocket Launch Due To Vehicle Subsystem Problem
Apr 24, 2025 -
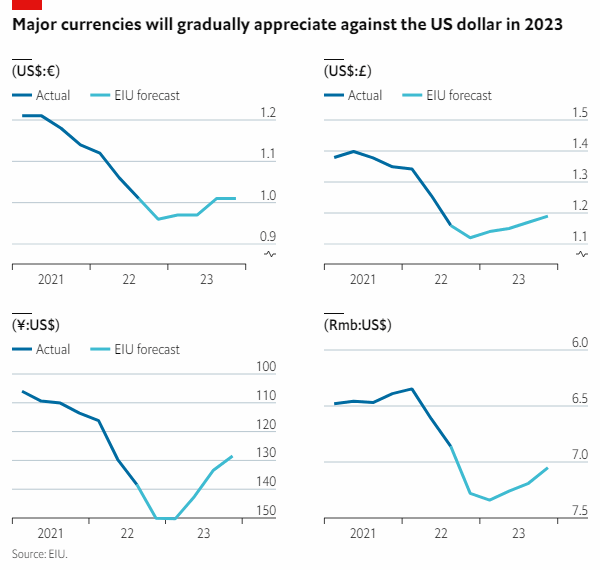 Trumps Fed Comments Impact The Usd Dollars Appreciation Against Key Currencies
Apr 24, 2025
Trumps Fed Comments Impact The Usd Dollars Appreciation Against Key Currencies
Apr 24, 2025
