Millions Stolen: Insider Reveals Massive Office365 Executive Email Compromise
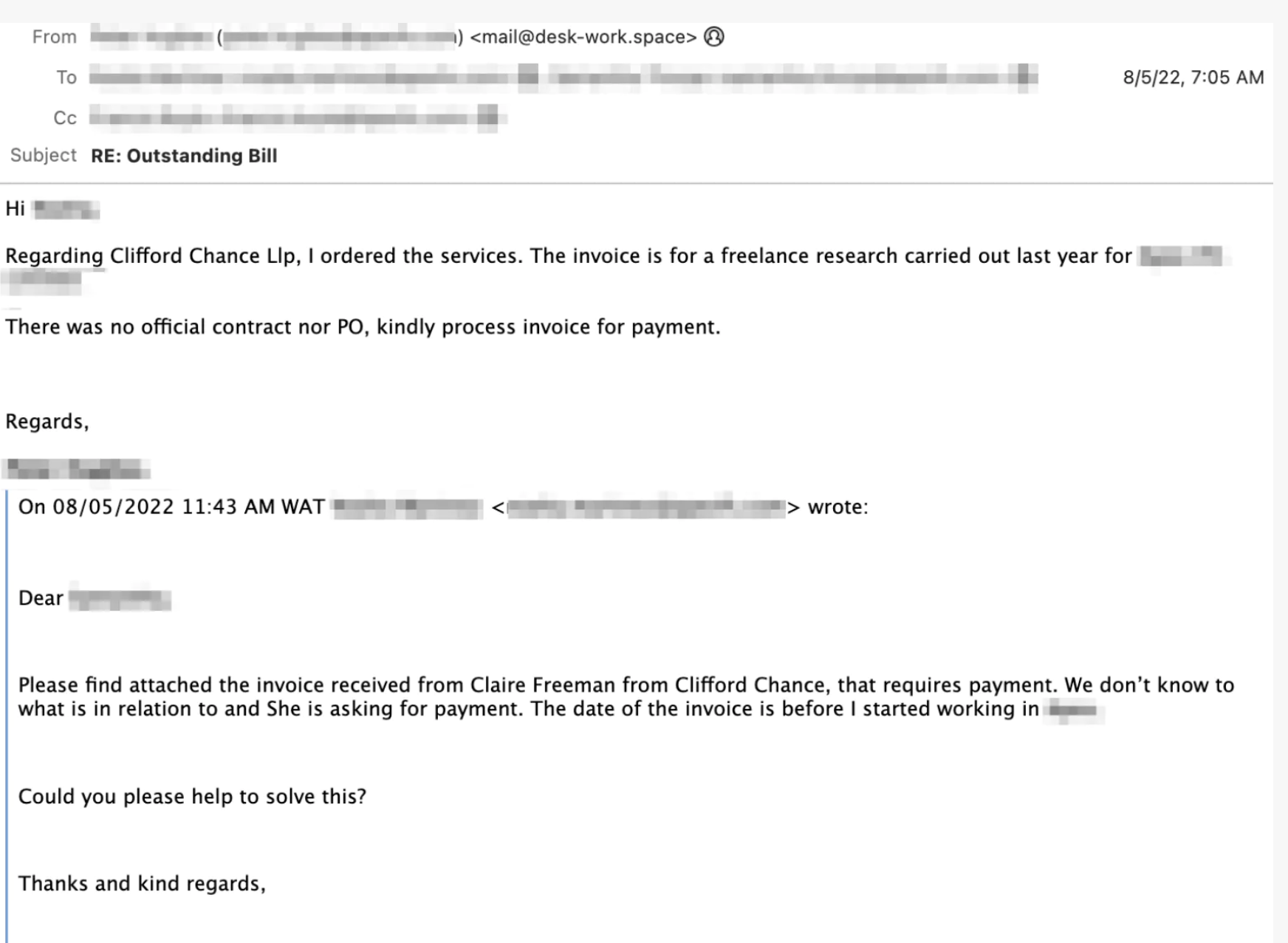
Table of Contents
Cybercrime costs businesses billions annually, and a significant portion stems from email compromise attacks. This article unveils a chilling case of Office365 Executive Email Compromise, revealing insider information about a massive breach resulting in millions of dollars stolen. We'll explore the vulnerabilities exploited, the attack's progression, and crucially, how your organization can avoid becoming the next victim. Prepare to learn the shocking truth about how easily seemingly impenetrable systems can be breached.
Understanding the Office365 Executive Email Compromise Vulnerability
Despite Microsoft's robust security features, Office365 remains vulnerable to sophisticated executive email compromise (EBC) attacks. Attackers target high-level executives, understanding that compromising their accounts provides access to sensitive financial data, strategic plans, and critical business information. Common attack vectors include:
- Phishing and Spear-Phishing: Highly targeted emails designed to trick executives into revealing credentials or downloading malware. These attacks often leverage the executive's reputation and relationships to increase their success rate.
- Weak Passwords/Password Reuse: Executives, like anyone else, can fall victim to poor password practices. Reusing passwords across multiple platforms creates a significant vulnerability.
- Compromised Third-Party Applications: Many organizations integrate third-party apps with Office365. A compromise in one of these apps can provide a backdoor into the entire system.
- Social Engineering: Manipulative techniques used to trick individuals into divulging confidential information or granting access. This can range from simple phone calls to complex impersonation schemes.
Implementing robust security measures like multi-factor authentication (MFA) is critical. Even seemingly secure Office365 features can be exploited if not properly configured and monitored. For example, attackers may exploit vulnerabilities in legacy protocols or leverage compromised API keys.
The Insider's Account: How the Millions Were Stolen
A source close to the investigation, who wishes to remain anonymous, provided details about the breach. The attack started with a seemingly innocuous phishing email targeting the CEO. This email contained a malicious link that, when clicked, downloaded malware onto the executive's computer.
The stages of the attack unfolded as follows:
- Initial Compromise: A spear-phishing email successfully bypassed the organization’s existing email security filters.
- Privilege Escalation: The malware granted the attackers administrator-level access within the Office365 environment.
- Data Exfiltration: Data was exfiltrated using a combination of cloud storage services and email forwarding to external accounts, carefully orchestrated to avoid detection.
- Target Focus: The attackers specifically targeted financial records, strategic partnerships, and sensitive client information held within executive-level accounts.
Social engineering played a crucial role. The attackers' success relied on the credibility and urgency created within the phishing emails, exploiting trust and time pressure to maximize their chances of success. The stolen data included millions of dollars in financial records, intellectual property, and crucial business strategies.
The Aftermath: Damage Control and Lessons Learned
The breach had a devastating impact on the organization, leading to significant financial losses, legal challenges, and reputational damage. The recovery process involved:
- Incident Response and Forensic Investigation: A team of cybersecurity experts was brought in to investigate the breach and contain the damage.
- Notification of Affected Parties: Affected clients and stakeholders were informed about the incident, a legally and ethically necessary step that adds to the crisis management burden.
- Strengthening Security Protocols: The organization implemented enhanced security protocols, including stricter access controls, improved MFA enforcement, and advanced threat protection.
Key lessons learned emphasized the need for:
- Employee Security Awareness Training: Regular and comprehensive training is critical to prevent future breaches.
- Robust Security Measures: Basic Office365 settings are insufficient; organizations need layered security solutions.
- Incident Response Planning: A detailed incident response plan can significantly reduce the impact of a successful breach.
Protecting Your Organization from Office365 Executive Email Compromise
Preventing similar attacks requires a multi-layered approach:
- Strong Password Policies and MFA: Enforce strong password policies and mandatory MFA for all users, especially executives.
- Regular Security Updates: Keep all software and patches up to date to mitigate known vulnerabilities.
- Security Awareness Training: Regularly train employees on identifying and responding to phishing attempts and social engineering tactics.
- Advanced Threat Protection: Utilize the advanced threat protection features offered within Office365 and consider additional third-party solutions.
- User Activity Monitoring: Monitor user activity for unusual login attempts and suspicious behavior.
- Data Loss Prevention (DLP): Implement robust DLP measures to prevent sensitive data from leaving the organization.
Regular security audits and penetration testing by external security experts are highly recommended. Consider investing in advanced security information and event management (SIEM) tools to enhance threat detection and response capabilities.
Conclusion: Safeguarding Your Business from Office365 Executive Email Compromise
The case highlighted underscores the significant threat of Office365 executive email compromise. The financial and reputational consequences can be catastrophic. Proactive security measures, combined with ongoing employee awareness training, are not just recommended—they're essential. Don't wait for a breach to occur. Review your organization's Office365 security posture today. Implement strong password policies, MFA, advanced threat protection, and regular security awareness training to safeguard your business from Office365 Executive Email Compromise and similar attacks. For more information on protecting your organization, explore resources from [insert reputable cybersecurity resource link here] and [insert another reputable cybersecurity resource link here].

Featured Posts
-
 Ai Digest Transforming Scatological Data Into A Thought Provoking Podcast
Apr 22, 2025
Ai Digest Transforming Scatological Data Into A Thought Provoking Podcast
Apr 22, 2025 -
 Microsoft Activision Deal Ftcs Appeal And Its Implications For The Gaming Industry
Apr 22, 2025
Microsoft Activision Deal Ftcs Appeal And Its Implications For The Gaming Industry
Apr 22, 2025 -
 Mapping The Countrys Emerging Business Hubs
Apr 22, 2025
Mapping The Countrys Emerging Business Hubs
Apr 22, 2025 -
 Ukraine Under Fire Russia Launches New Aerial Barrage Amid Us Peace Push
Apr 22, 2025
Ukraine Under Fire Russia Launches New Aerial Barrage Amid Us Peace Push
Apr 22, 2025 -
 Microsofts Activision Deal Faces Ftc Appeal Analyzing The Future Of The Merger
Apr 22, 2025
Microsofts Activision Deal Faces Ftc Appeal Analyzing The Future Of The Merger
Apr 22, 2025
